Different types and benefits of Access control system:Mandatory Access Control System
Access control is the process of identifying
people and determining the level of security access to an electronic system or
physical site based on policies and procedures set up by your organization. Modern
access control systems identify a person, verify and verify their identity
cards, and give the person only the keys for the doors and digital resources
they need to access.
Access is granted through several steps to verify
that this user can access the requested resource. These steps are typical.
Ø
Identity
verification
Ø Authentication
Different Types of Access Control Systems
Discretionary Access Control System
Optional Entry and Exit Management are suitable
for households and small businesses that need security in one or two doors. It
is less restrictive than other access control systems, and end users (such as
homeowners and corporate owners) have full control over who can enter and
leave. You can also easily set your security level, set permissions for others,
or give someone access by telling you your entry key or your entry PIN. A
standalone access control system lets you concentrate security on the door
itself.
Mandatory Access Control System
On the other hand, mandatory access control
is a form of access control with the most restrictions that gives control and
management of the system and access points only to the system owner or the
administrator. End users and employees have no control over permissions and
access and can only access points authorized by the system owner. Furthermore,
the administrator can only change the settings defined by the system parameters
themselves, and since they are programmed in this way, they cannot be avoided.
All users are classified, labeled, and allowed to
enter, access, and exit specific points according to their permissions and only
the specified classification level.
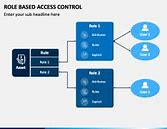
Role-based Access Control System
They provide access rights according to the
individual's position in the organization, also called discretionary access
control. This system associates predefined roles with specific privileges.
Administrators can assign only the access rights required for their work to
individuals.
Rule-based Access Control System
Rule-based access control is also called RBAC or
RB-RBAC. Rule-based access control dynamically assigns roles to users based on
criteria defined by custodians or system administrators. For example,
rule-based access control is the chosen tool if a person can access a file only
at a certain time.
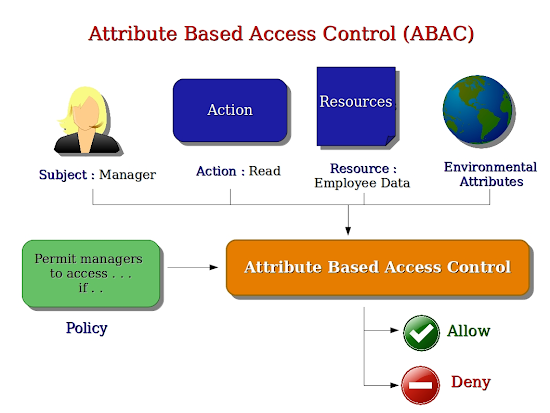
Attribute-Based Access Control (ABAC)
The Attribute-Based Access Control (ABAC) model
is often described as a finer granularity of role-based access control because
it has multiple attributes required to access. These attributes are associated
with the subject, object, action, and environment. For example, a sales
representative (subject) may access a customer's record (object) from the
office during office hours to update information (an action) (environment).
Benefits of Access Control
1. Keep track of your room
Many companies have valuable equipment and
physical assets on site. The access control system grasps who is going in and
out and confirms that no one is sneaking into the building. In a large
enterprise with many employees, it is difficult for everyone to know who is an
employee and who is not. Access control systems help prevent strangers from
unnoticed and entering the room.
2. Understanding employees
The access control system can organize the
confusion when there are multiple times when employees enter and leave and can
inform you when employees are in the building at a time when they should not
enter and leave. You can also see who is in and who is not.
3. Protect sensitive documents and data
Many companies have documents and data that
should be inaccessible to everyone. Access Control Systems can restrict access
to certain areas of hardware or software where this information is stored.
4. Prevention of theft and accidents
Access to the storage of valuables and hazardous
materials can be restricted to authorized or specially trained employees by
using the access control system.
5. Multi-Property Protection
The access control system can grant access to
employees who need to enter multiple or all buildings.
6. No Longer Worrying about Keys
When employees retire and do not return their
keys, companies are left with the expense of creating new keys and possibly
replacing them. The same is true when an employee loses his company key. Also,
if an employee leaves the company and is unscrupulous, the employee may
re-enter the building and cause damage.
Final
Words
If your business has
sensitive areas that only authorized people can enter, the best way to control
security is to implement an access control system. The system allows users to
permit or deny access to any part of the site, including parking lots,
elevators, warehouses, and residential entertainment rooms, using devices such
as key cards, fobs, and biometric scanners. Every time you use a card reader or
biometric scanner, the system keeps track of your entry and exit.
citation:
https://resources.infosecinstitute.com/certification/access-control-models-and-methods/





Comments
Post a Comment